Table of Contents
Introduction
Traditional network services use a client-server approach. Clients like you must connect to a server to obtain the official copy of the shared resource. This facilitates synchronization (because the server has access to the most up-to-date version), but it is highly centralized. This may be problematic because it requires faith in the server, which may be at risk from DoS assaults.
Blockchain promises to be a completely decentralized system. Every node in the blockchain network can keep a copy of the distributed ledger, and blockchain consensus mechanisms update the official version.
A node is a component of cryptocurrency essential for operating the most prominent cryptocurrencies, including Bitcoin and Dogecoin. Furthermore, it is a crucial part of the Blockchain system, the decentralized ledger that records cryptocurrency transactions.
It’s becoming increasingly important for people to learn the fundamentals of Bitcoin and other cryptocurrencies as their popularity grows. Of course, this is true in any industry, but the novelty of cryptocurrencies increases its appeal.
The term’s usage extends beyond the realm of cryptography.
In simplest terms, a node is a connection or hub in a communications network. Any device or hardware part of a network that can generate, receive, or transmit data is considered a node.
A node is a computer part of a cryptocurrency network that can generate, receive, and transfer cryptocurrency.
The explanation may change depending on the specifics of the protocol. A home office might feature a fax machine, three computers, and a document storage server. In this case, there are five nodes in the network, each using a unique MAC address to communicate with other nodes. In the Blockchain community, “node” is shorthand for “computer.”
What are Blockchain nodes?
Blockchain nodes are network stakeholders, and the devices they employ to monitor the distributed ledger and operate as communication hubs for various network activities obtain permission to do so from the blockchain.
A Blockchain node’s primary responsibility is to determine whether or not the blocks of network transactions that come after it are legitimate. Furthermore, assigning a unique identifier to each node in the network allows for easy differentiation between individual nodes.
An example of “proof of work” is Miners on a blockchain network like Bitcoin (BTC) or Monero (XMR) are accountable for the following.
To participate in the blockchain, only “full nodes” must keep a copy of every transaction. These nodes are accountable for confirming the legitimacy of blocks and transactions.
On the other hand, lightweight nodes only need to download block headers to verify transactions. Therefore, they can use less space. Neither of these simplifications of a full node always includes a block reward.
What Do Nodes Do?
Nodes are critical to the blockchain environment because they do everything. In a peer-to-peer system that doesn’t have a central server, everyone works as both a client and a server. Therefore, nodes have a wide variety of protocol-specific (rather than software-specific) tasks.
Protocol, Not Software
A blockchain is not a unique piece of software like many other Internet applications. Instead, it is a set of rules. The only prerequisite for using a service (like Skype) is that nodes communicate according to the regulations of the service rather than requiring that all users execute the same executable.
One example is HTTP, the system that defines how websites work. The algorithm specifies the sequence and construction of network packets, but nobody cares what software you use.
Because of this, there are many different web servers (like Apache, IIS, etc.) and web clients (like Chrome, Firefox, Safari, etc.). Since these servers and browsers decided to follow the protocol, they can talk to each other without any problems.
Some blockchains are combined with more than one piece of software, while others only have one. Cross-comparison is always a good idea when picking blockchain tools to run.
Common Node Tasks
The node’s job is to put the blockchain into action and run it. Each node can store a full copy of the distributed ledger and, if it does, can change it based on what the network agrees on. So, nodes can participate in various activities, such as processing transactions, making blocks, and managing the record.
Transaction Processing
Transaction handling is one of the most common jobs that nodes have. To add their transactions to the distributed ledger, node users must send them to the node.
The node is in charge of sending these transactions to the rest of the network and sending any transactions it gets from other nodes to its peers in the network.
Stop The Creation
Adding new blocks to the chain is how the blockchain is changed. These blocks are what the global ledger uses to store its information.
Someone must collect this data into a block and send it to the rest of the network. Since there is no central computer in the blockchain, this is also the responsibility of the nodes. A blockchain consensus method chooses a node to create the next block. They do the work of making the next block and starting to send it out, and they get paid for it.
Ledger Management
Lastly, it is up to the nodes to make sure that the distributed ledger is kept and accessible in the right way. Every node could store an entire copy of the spread ledger. Because not all users of a blockchain network are also nodes (some people use Bitcoin to make purchases or investments), these nodes may, at times, have to deliver a copy of specific areas of the blockchain to a user to certify that a transaction was successfully added to a distributed ledger.
Types of Blockchain Nodes
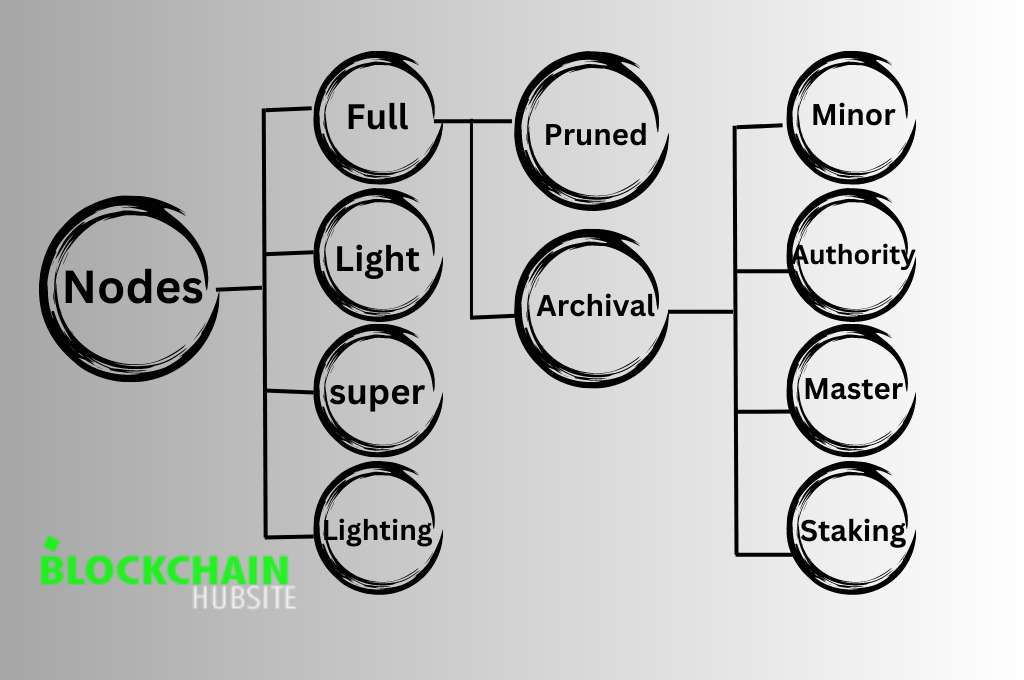
A blockchain can have various node types, and each kind is classified based on its functions.
Following are different types of nodes in blockchain.
1. Full Nodes
The full node is the program that verifies blocks and transactions. A node is a device in a network that performs administrative tasks. Nodes keep track of a lot of information on the network, such as sharing information and wallet assets on a blockchain.
The full node validates blocks and transactions from other nodes and contributes to the network by broadcasting these items to other nodes. A full node can announce transactions to the network. When a transaction occurs in a user’s wallet, the full node alerts the wallet and offers its services to the user’s computer. Computers cannot join the end-to-end network without enough nodes for transactions. The greater the number of nodes in a blockchain network, the greater its decentralization.
How Does Full Node Work?
Nodes in a blockchain network perform administrative and regulatory functions. Blockchain networks require consensus methods to operate correctly. The network nodes are accountable for ensuring the legitimacy of each transaction added to the blockchain. Once everyone agrees, the nodes verify the events and add them to the distributed ledger, also known as the blockchain.
One of the functions of a full node is to maintain a record of all of the network’s transactions that have been validated. Depending on the length of the blockchain, full nodes need varying amounts of information. A full node ensures the integrity of transactions by recording and archiving all of the network’s blockchain’s past dealings. If the network ever collapses, we can restore it because full nodes have a copy of the blockchain’s history.
Advantages and Use Cases
Security: Full nodes verify trades and apply consensus protocols to ensure the blockchain is legitimate.
Because they check all transactions and blocks independently, hostile actors have more difficulty influencing the network. Users can have complete control over their transactions and the safety of their funds by running a full node.
Data Privacy: Users can protect their personal information when using full nodes because they can independently verify their transactions. Users of lightweight or SPV (Simplified Payment Verification) wallets rely on complete nodes for reliable data. Users that run their full node can validate their transactions and protect their private wallet addresses from being shared with other nodes.
Network Stability: Stability of the Blockchain Network: Full Nodes Play an Important Role in Maintaining Blockchain Network Stability. They help spread transactions and blocks across the network by keeping a full copy of the blockchain. In a distributed system, full nodes are information relays, spreading data, and keeping everyone updated.
Consensus Participation: Full Nodes are an Essential Part of Blockchain Networks. They verify transactions, apply consensus rules, and help make decisions. Depending on the blockchain network, full nodes can participate in consensus procedures like proof-of-work (PoW) or proof-of-stake (PoS). By running a full node, individuals can actively participate in network governance and consensus.
Supporting Decentralization: Full nodes aid decentralization since they disperse the blockchain’s transaction history among many users. They ensure that no single entity or group has authority over the entire network, which helps to prevent the misuse of centralized power. Users help make the decentralized system more robust by operating a full node.
Development and Testing: Using full nodes is crucial for developing and testing blockchain initiatives by researchers and developers. Developers can create and test applications, smart contracts, and other blockchain-based features with full access to the blockchain’s data. In other words, full nodes make it possible for programmers to explore the functionalities of the blockchain and create novel applications.
Block Explorer Services: Block explorers are web-based tools that enable users to browse and study the blockchain’s data, and they rely on full nodes as their backbone. Individuals can help increase the accessibility of block explorer services by hosting a full node, which will increase the network’s transparency and provide valuable insights.
2. Mining Nodes
Miner nodes validate transactions and add new blocks to the blockchain. These nodes solve complex mathematical problems to make new partnerships and earn cryptocurrency rewards.
Mining calculations require specific hardware and software on miner nodes. Large mining pools or individuals can operate them by purchasing and using the necessary hardware. Miner nodes play a crucial role in the Blockchain network by verifying and adding new transactions to the blockchain.
Mining Algorithms and Equipment
What is proof of work?
The miners of the proof-of-work consensus technique employ potent computers to solve complex issues. Trial and error fix the problems. The first miner to solve the cryptographic riddle or the cryptographic equation receives the privilege of adding new blocks to the blockchain. The blockchain receives digital cash when a miner verifies the block. The miner will also receive coins as compensation for their work.
A proof-of-work system necessitates the employment of powerful computers that consume lots of power. Transaction times may get slower as the cryptocurrency network expands since it consumes so much passion and energy.
To compromise the blockchain’s security, a malicious actor must control 51% of the network’s computer power, which is extremely unlikely. As the community adjusts the blockchain’s protocol, the chain can split into two blockchains, a process known as “forking.” The original’s history changes in a new direction to prevent duplicating transactions or spending.
Any miner can switch to the newer branched network or keep working with, the older one. This makes it much harder for a bad actor to take control of 51% of the network since they would have to split their computing resources between the two blockchains and support both of them.
What is proof of stake?
Before using proof of stake to verify transactions, miners pledge digital currency. To prove blocks, miners must risk some of their cryptocurrency. Additionally, miners disclose how long they have been in the business of verifying trades. A computer program uses a random number generator to select the individual who will verify each transaction. The program also takes into account the total amount of money at stake as well as the individual’s level of experience verifying transactions in the past.
After verifying a block, the miner receives cryptocurrency for their fee and stake. If the miner makes a mistake in verifying the block, they could lose a substantial amount of coins. By requiring miners to risk their own money, we add another layer of protection against theft and other forms of fraud.
As an alternative to proof of work, the proof-of-stake system considers energy consumption, environmental effect, and scalability issues.
The major drawback of proof-of-stake is the high initial cost of acquiring a network stake. If a blockchain splits, a validator obtains a duplicate copy of their stake because there is no track record of performance, giving those with the most money authority. It is possible for the validator to double-spend their coins if they support both paths via the fork.
Discussion of mining hardware and software requirements
The success of cryptocurrency mining operations is heavily dependent on the necessary mining hardware and software.
Mining Hardware: “Mining hardware” describes the specialized hardware used to do the computations necessary for mining cryptocurrencies. The main focus is mining cryptocurrencies like Bitcoin and Ethereum that operate on proof-of-work (PoW) consensus methods. In selecting mining hardware, keep in mind the following:
a. Hashing Power: The mining hardware’s hashing power, which measures in hashes per second (H/s), shows how well it can solve complex math problems and find new blocks. When more hashing power is available, mining can proceed more rapidly and efficiently.
b. Energy effectiveness: Mining hardware uses a lot of power. Hashes per watt (H/W) is a valuable metric for measuring energy efficiency, which is crucial for keeping overhead down.
c. GPU vs. ASIC: Graphics Processing Units (GPUs) and Application-Specific Integrated Circuits (ASICs) are the two most common types of mining devices. Although their hashing power may be lesser, GPUs offer greater versatility because they can mine various coins. ASICs, on the other hand, fit a specific cryptocurrency, have greater hashing power, and are less flexible.
d. Noise and Cooling: Mining equipment produces heat and noise when used. Workplace comfort and productivity depend on access to adequate cooling systems and noise reduction techniques.
e. Mining Software: Mining software facilitates communication between mining devices and the cryptocurrency network. It controls the mining operation, establishes a link to the blockchain, and supplies fundamental features. The essential elements of mining applications are as follows:
a. Mining Client: The mining client is the software that communicates with the mining pool or cryptocurrency network and runs on the mining hardware. It enables miners to connect their hardware, get work tasks, and submit solutions.
b. Compatibility: The mining software must be compatible with the user’s operating system and mining hardware. Finding software that works with your specific hardware setup and cryptocurrency of choice is possible.
c. Pooling and Solo Mining: Mining software allows both solo mining (mining on your own) and pooled mining (joining a group of miners). By combining their computing resources, miners using pooling software have a greater probability of discovering blocks and earning rewards on a more consistent basis.
d. Monitoring and Management: Many mining programs include built-in tools and functions for monitoring data like hash rate, temperature, and power consumption. Some programs also support remote management, giving miners commands from a distance.
e. Safety and Updates: Mining software should be updated frequently to fix security flaws and take advantage of enhancements to its performance. The security and dependability of open-source software with a vibrant development community are generally higher.
It’s crucial to note that mining gear and software requirements differ by cryptocurrency and mining algorithm. That’s why it’s so important to do your homework and pick mining-specific hardware and software.
3. Masternodes
Masternodes, in the simplest terms, are servers present in decentralized networks. It differs from regular nodes because it can do specific functions that normal nodes can’t. Instantaneous and private transactions and direct transmission are just a few of the many services they offer.
Masternodes are central nodes in a network; they each have their pros and cons. So, no two master nodes are the same, and each system handles them differently. Many beginners get them mixed up because master nodes and crypto mining share some similarities but are fundamentally different activities.
Functionality
Functionality: Within the blockchain network, masternodes perform several roles, including:
Increased Network Safety: Masternodes strengthen the safety of the network by contributing to consensus procedures. They verify trades, stop double spending, and enforce protocol rules to protect the integrity of the distributed ledger.
Instant Transactions: Masternodes provide instant or very instant transaction confirmations. Technology like InstantSend helps them achieve this goal by allowing instant, safe transaction verification without the need for several block confirmations.
Private Transactions: Some master node-based cryptocurrencies have extra privacy tools like PrivateSend or CoinJoin. These characteristics improve user privacy and fungibility by hiding the sender and receiver of transactions.
Governance and Voting: Most of the time, master node operators can participate in network governance by voting on ideas or changes to the protocol. The stakeholders in a blockchain network can have a role in its future thanks to this decentralized governance framework.
Network Scalability: Masternodes can help the blockchain network grow by taking over some of the regular nodes’ jobs. The network can process more transactions and use resources more effectively because of master nodes.
Incentive Mechanism: Masternode operators receive rewards with digital currency for providing services and collateralizing a set quantity of coins. These bonuses not only increase revenue for node operators but also increase participation.
How to Earn a Passive Income with Masternodes
Using master nodes to make passive income depends on several things. This includes the cost of the network and cryptocurrency, any necessary initial investments, ongoing expenses, and any price variations. However, participants can keep their assets by holding rather than selling when they lock up collateral to become a master node. Therefore, becoming a master node only results in losses if the value of the collateral asset decreases.
A passive income with master nodes may be possible if the rewards from validating transactions exceed the costs. There are further advantages to running a master node as well. Masternodes, for instance, offer a distinct viewpoint on the operation of blockchains. In addition, master nodes are accountable for the network’s overall health.
The decision to become a master node is not without risk, though. Masternodes’ promise of passive income is tempting, but investors should remember that cryptocurrency prices fluctuate wildly. As a result, collateral value is at risk of decline (but equally at risk of appreciation). It may be challenging to sell the crypto asset necessary as collateral if it is only available in thin or illiquid markets, even if the idea is novel and helpful. Furthermore, failure to maintain consistent uptime or keep your master node up to date may result in a loss of profits.
4. Staking Nodes
Staking nodes validate blockchain transactions following the Proof of Stake consensus model. The process is known as staking when a staking node holds cryptocurrency as collateral. The system randomly chooses which staking node to process transactions and adds them to the distributed ledger. A staking node may consist of a single user or a group working together. Staking nodes consume much less power than miner nodes when validating transactions.
Keeping a cryptocurrency wallet online around the clock is necessary for maintaining a stake, unlike the expensive hardware required for mining. Users must install the coin’s core wallet and keep the complete blockchain on their device to qualify as full archival nodes and participate in staking. Staking is a game of chance with less assurance than mining but a lower entry barrier.
What are staking rewards?
“Staking” comes from putting something “at stake,” which means putting coins or tokens in a staking pool for a specific time.
When cryptocurrency owners put their coins “at stake” in a stake pool within a network, they get a share of the staking benefits given to the pool in return. This is similar to getting interest payments on savings in the traditional financial world.
Many cryptocurrencies pay out staking rewards in the network’s original coins or tokens. Still, other blockchains create their own or different coins and tokens as staking rewards for the blockchain’s internal operations.
How are staking rewards generated?
The total number of individuals staking, transactions, and other factors can all influence staking payouts. Participants get the right to add a new transaction to the blockchain after putting their coins into a stake pool to help with approval. Depending on how many tokens a node has, it can be the one to confirm a transaction.
A validator receives staking incentives immediately after choosing and verifying the transaction. The validator then sends a portion of the staking rewards to the people who gave their coins to the validator. The staker will pay a proportion of the total stake if a transaction fails or the elected validator is unavailable.
5. Validator Nodes
- Many forms of blockchain networks have validator nodes, distinct kinds of full nodes that can participate in the network’s consensus process.
- These validator nodes usually collaborate to verify, vote on, and record network transactions.
Validator Node Components
Each validator node saves a copy of the ledger and talks to the other nodes in the network all the time to ensure that all the copies are the same as new data gets added. However, since the entire ledger is not under the authority of a single institution but rather by a distributed network of validators, the network requires less confidence than the conventional alternative and is immune to censorship. These are in charge of validating the blockchain.
Each validator agrees on the ledger’s state using a consensus algorithm. This algorithm is different for each blockchain. But to understand how validator crypto nodes work, we need to look more closely at each part they have.
Execution
Execution is the first thing we need to talk about when it comes to validator nodes. Execution is a part of the validator node, which handles how a block of transactions executes and tries to keep a temporary state.
But it’s also important to know that the execution component can keep an in-memory copy of the results of the execution until the consensus components can commit the blocks to the distributed database. Then, the execution component can use the virtual machine to perform the transactions.
Mempool
The Mempool is another crucial part and function of validator nodes that we need to look at. This part of the system is in charge of keeping a stack of transactions in memory. These transactions have been sent but haven’t been agreed on or run yet. The nodes copy this buffer and share it among themselves.
If you’ve seen a JSON-RPC service in a full node, it’s talking about the node’s mempool. It can even do initial checks on the requests, which protects the other parts of the validator node from fraud or even just a lot of inputs.
The mempool receives transactions that pass the first tests. This mempool then gets shared with other validator nodes.
Consensus
The Consensus component is another essential part that ties everything together. Through it, the validator node shares the responsibility of putting the transactions in the correct order and can agree on the result of the execution by taking part in the consensus protocol with other validator nodes in the network.
Blockchains utilize different consensus processes; therefore, how they do this can vary. In any case, the consensus process is a big part of the node and plays an important role.
Virtual Machine
The term “Virtual Machine” is probably one you’ve encountered at some point in your research about blockchains. If you didn’t know what this was about, the virtual machine runs the Move program in a submitted transaction. After that, it can decide what the final results will be.
So, a validator node’s mempool uses the virtual machine components to check the transaction, while the execution component uses it to run the transaction as a whole. This is another essential part of the validator nodes.
Storage
The validator node uses its storage component to agree on blocks of transactions and their execution results.
With this network storage, meeting storage needs and ensuring they’re always available is much easier.
State Synchronizer
In addition to all of the above features and parts, it is essential to note that validator nodes also use a “state synchronizer.” This state synchronizer lets them catch up to the latest state of the blockchain network so that every node can be as up-to-date as possible.
How to Make a Validator Work
It’s not as complicated as you think to run a validation node. This is because there are a lot of different blockchain networks out there, and each one has its consensus process and ways to get things done. Many of these networks have been able to organize this process in many different ways.
1. a validator server must often meet specific hardware requirements before starting. These will include needs for the central processing unit (CPU), random-access memory (RAM), disc drives (DISC), and graphics processing units (GPUs).
2. Software needs to follow this. Usually, a user who wants to set up a validator node will be requested to install a particular operating system, like Ubuntu (Linux), along with other prebuilt binaries.
3. Then there’s the matter of configuring the network’s settings. Each validator node will typically require ports to be available to the internet for incoming and outgoing connections.
4. The next step is system tuning, which each network typically completes in its way.
6. Light Nodes
What is a light node?
A light node is a low-cost Ethereum node that needs to download Ethereum block headers to conduct transactions on the network. Unlike full nodes and archive nodes, which are more complex Ethereum nodes, a light node is the simplest node you need to get started.
Light nodes use the least data possible to interact with the Ethereum blockchain. They get all the other information from full nodes, which keep the full blockchain data and verify and validate the blocks.
How do light nodes work?
Light nodes engage with the Ethereum blockchain only when they need to. They do this by using block headers, which summarize what is in each block. If a light node needs more information, it will ask for it from a full node. This process makes it possible for light nodes to connect with the network in a way that saves gigabytes of storage and megabytes of bandwidth.
What are the benefits of light nodes?
The most significant benefit of running light nodes is that they are easy to set up because they only need a small amount of data and storage and are also cheap to run.
Users can run light nodes on devices like computers and phones, which gives them much more access to data on the blockchain. On the other hand, full and archival nodes require a lot of hardware, storage space, and maintenance time to run. Light nodes are faster, more efficient, and easier to use than full nodes.
7. Archive Nodes
What are Archive Nodes?
In a blockchain system, archive nodes are a special kind that records all previous transactions. They are essential to the network’s integrity and transparency because they record all immutable activities. This means anyone can check the blockchain’s ownership and authenticity of goods.
Archive nodes differ from other blockchain nodes because they need much storage space and computing power to keep a full copy of the blockchain’s history. Their role is to guarantee the security of the blockchain and its applications in exchange for tokens or currencies from the network. People often say that archive nodes are “the immune system of blockchain technology.”
How Do Archive Nodes Work?
Archive nodes keep a full copy of the blockchain’s log of transactions. Archive nodes receive a copy of each new blockchain block and store it locally. This process occurs for every block in the chain, ensuring archive nodes have a comprehensive and up-to-date record of all transactions. Validators can review the archive node’s past transactions to guarantee that a new block or collection of transactions (in Shardeum) follows the blockchain’s rules and consensus methods.
In addition, archive nodes permit the replay of past transactions. This feature can simulate different situations, such as arbitrary transactions. Using the historical data from the archive node, validators and developers can recreate the state of the blockchain at a certain point in time and mimic the execution of any transaction. This helps people understand the effects of these kinds of deals and judge their validity and impacts.
Because archive nodes store every blockchain transaction, they need much storage space. But the value they add makes an immutable and unchangeable record of the blockchain’s past. This is essential to ensuring that blockchain networks are trustworthy and transparent.
8. Pruned Nodes
Pruned nodes are a type of blockchain node that can do almost everything a full node can do. The only difference is that pruned nodes don’t have a full copy of the blockchain. Before this type of node can do anything, it has to download the whole blockchain. Then it removes blocks. The oldest comes first in the process. And it keeps going until the node only keeps the most recent transactions or reaches a size limit set before. For instance, if a node operator specifies a maximum data size of 100 MB, a pruned full node will only save the last 100 MB of transactions.
For instance, if the maximum size is 550 MB, the node will only save the most recent.
How does a pruned node work?
How can you “prune” a blockchain, and what does it mean to “prune”? Also, when we talk about “pruning,” we suggest reducing the size of the blockchain to a point where we can make a safe registry with a specific size.
Think of the blockchain as a big tree with many branches and leaves connected from the newest to the oldest. This connection lets you track all of the blockchain’s actions from the most recent back to its beginning or root. But this tree is so big that you can’t put it all in one place.
In light of this difficulty, you decide to focus on the final branches and their data, resulting in a much smaller but identical replica of the original tree. So you decide to cut off its last few branches and use them to make a copy tree that will follow its past from that point on. In short, you make a child tree, a copy of the blockchain. The child tree’s first leaves confirm the parent tree’s history, which is the original blockchain, and continue the history from that point. The original tree and your copy will be the same from the point of pruning.
The Bitcoin program does this exact thing. That is, it downloads the whole tree, which is the original blockchain, checks it to make sure the download is correct, then stores only the part of the tree you desire and throws away the rest. At this point, the blockchain on your computer is a child tree, a partial replica of the leading blockchain, and all transactions between the two are identical and have the same validity.
Merkle and Merkle Root trees are like the pruners for the blockchain.
The blockchain typically refers to a chain, so why call it a tree? Merkle trees and Merkle roots are the structures that make it possible to “prune” a blockchain.
First of all, Merkle Trees are the blocks’ basic building blocks and the hash that goes with them. Remember that the point of a Merkle tree is to use cryptographic functions to put together and connect a lot of information. At the end of this cryptographic synthesis process, you get the “Merkle Root,” a one-of-a-kind hash that will not exist again. It comes from putting all this information together. This method allows for the Bitcoin block’s transactions to be inextricably linked to the block they’re found in.
The arrangement of the blocks in a blockchain is another factor that contributes to their stability. This is because the Merkle Root is one of the fundamental pieces of information required to establish a cryptographic connection between individual blocks. The Merkle Root of each new block is very close to the Merkle Roots of the blocks that came before it. In other words, every fresh Merkle Root in a block confirms and verifies the past of the blocks before it. Even a seemingly insignificant change might render the entire history meaningless in this approach.
Still, we can see what a pruned node in Bitcoin does more straightforwardly: it just downloads the blockchain, checks that the Merkle Roots are correct, and then cuts it at a certain point to make a copy. From that point, the Merkle Root continues to grow and change the same way the original blockchain did, except that we have a smaller replica that is easier to work with.
Blocks that can fit in its memory, but it will still need to verify every block in the blockchain. Even though it is a pruned node, it is still a full node and can check transactions and take part in reaching a consensus.
Pros And Cons
Pros: It needs about 5 GB (a little more than 5 GB) by default. You don’t need to keep the whole blockchain information on your computer. You can run a pruned node to learn how Bitcoin core works without putting much pressure on your computer’s storage space.
Cons: Your machine doesn’t have a full blockchain database.
After loading a wallet, you must resync it with the blockchain.dat file containing data from outside your pruning node. I find this very annoying.
9. Super Nodes
Supernode Proof-of-Stake, also called SPoS, is a good algorithm for reaching an agreement across many nodes that is resistant to 51% attacks. With SPoS, we can keep the best parts of Proof-of-Stake while allowing for massive scalability and transaction throughput.
SuperNodes vs. Full Nodes
The most significant difference between ‘Supernodes’ and ‘Full Nodes’ is that ‘Supernodes’ act as minting pools in the minting economy by creating blocks to get rewards and help VSYS Coin users. They help ensure the V Systems blockchain works well and provides a stable network for long-term growth.
Scalable and Stable Virtual Economy
Supernode minters use their coins and coins leased from other users to make blocks. The people who own VSYS Coins will get a prize in the form of interest. Since equal minting right gives all supernodes the same status and output, an equilibrium is a built-in force that balances the ecosystem and eliminates the threat of control seen in Bitcoin and other PoS ecosystems.
A virtual economy that can grow and is stable
Supernode minters use their coins and coins leased from other users to make blocks. The people who own VSYS Coins will get a prize in interest. Since equal minting right gives all supernodes the same status and output, an equilibrium is a built-in force that balances the ecosystem and eliminates the threat of control seen in Bitcoin and other PoS ecosystems.
Running a Supernode and Traditional Minting
When you challenge an existing supernode with a smaller MAB than yours, you get the right to take part in minting and become a supernode. The Supernodes are the nodes that have the highest total MAB level. They help mint new coins and earn money from the network. Supernodes make their own rules about rewarding the people who use them.
10. Authority Nodes
In centralized blockchains, authority nodes serve an essential purpose. The people who own these networks will choose who will verify deals. For example, network members vote on who gets to validate the next block under the Delegated Proof of Stake system. However, technically speaking, authority nodes have all the same properties as full nodes.
Benefits of Authority Nodes
Consensus and Security: Authority nodes help the blockchain network’s consensus process work. They participate in the consensus protocol and check the legitimacy of transactions to ensure that only legitimate ones have access to the blockchain. Having known entities act as authority nodes makes the network safer against malicious actions like double-spending or 51% attacks.
Improved Scalability: Authority nodes can improve the scalability of blockchain networks. By giving validation and agreement of transactions to a small number of authority nodes, the network can process transactions faster and handle more transactions at once. This method lowers the work we need to do to reach a consensus, speeding up the confirmation of transactions and making adding more users easier.
Network Governance: In blockchain networks, authority nodes often play a crucial part in running the network. They can suggest and vote on changes to the network’s protocol or settings. This governance system helps things simpler to make decisions and come to a consensus on changes or upgrades to the network. This leads to better management of the network and its growth over time.
Trust and Transparency: Including authority nodes can make a blockchain network more trustworthy and open. Since trusted groups or people run these nodes, other participants are more likely to trust the validation and consensus work they do. This makes it easier for users, investors, and businesses to trust the network and pushes them to use it more.
Regulatory Compliance: Authority nodes can help with regulatory frameworks and legal needs. Implementing KYC processes, AML safeguards, and other compliance-related operations is much simpler when certain businesses receive designation as authority nodes. This trait benefits blockchain networks that want to bridge the gap between traditional financial systems and decentralized technologies.
Conclusion
Blockchain nodes are the basis of a decentralized ecosystem, ensuring that transactions are safely verified and recorded. Each type of node has a specific role in the network’s functionality, ranging from transaction validation and block creation to delivering additional services and features. Understanding the many types of blockchain nodes is critical for understanding the complexities of blockchain technology and its wider implications for various businesses and applications. As the blockchain ecosystem grows, these nodes will continue to adapt and play an important role in developing the future of decentralized networks.
FAQs
1. How many nodes are there in blockchain?
The number of nodes in a blockchain can vary and is continually changing as new nodes join or leave the network.
2. Are there different types of nodes?
Yes, there are various types of nodes in a blockchain network, including full nodes, lightweight nodes, and masternodes.
3. How many types of Bitcoin nodes are there?
There are three kinds of Bitcoin nodes: full nodes, pruned nodes, and mining nodes.
4. How many kinds of nodes are available?
The types of nodes available vary depending on the blockchain network, but common types include full nodes, masternodes, and validator nodes.
5. What are 3 examples of node?
A full Bitcoin node, an Ethereum masternode, and a Cardano staking node are all examples of nodes.
6. How many StrongBlock nodes are there?
The number of StrongBlock nodes can vary and is subject to change as the network grows.
7. Can you make money with strong nodes?
Yes, it is possible to earn money with strong nodes by engaging in network activities and earning rewards.
8. How do I buy nodes?
Nodes cannot be purchased directly; instead, to become a node, you must typically participate in the network’s consensus procedure.
9. What is the maximum number of nodes in most network?
The maximum number of nodes in most blockchain networks is not fixed and can grow over time as new nodes join.
10. What are the best crypto nodes to run?
The best crypto nodes to run depend on your interests and investment goals, but popular possibilities include Bitcoin, Ethereum, and other major cryptocurrencies.
11. Can I become a blockchain node?
Yes, in most circumstances, you can become a blockchain node by installing the required software and completing the network’s requirements.
12. Do nodes mine crypto?
Yes, in most circumstances, you can become a blockchain node by installing the required software and completing the network’s requirements.